Cybersecurity &
Defense
Advice, Strategies
and Solutions to protect your digital assets.
How
we work? > Trust, Safety and Security.
WE
TAKE ACTION.
Our solutions align with your specific requirements, available resources, and risk tolerance, ensuring tailored and effective security measures that meet your unique business needs.
WE APPLY CRITICAL THINKING.
WE NEVER TRUST, ALWAYS VERIFY.
ZERO-TRUST is the paradigm shift to approach security, focusing on the principle of "never trust, always verify". We help you meet various compliance requirements by ensuring rigorous security measures and continuous oversight.
LEADING INDUSTRY FRAMEWORKS AND OUR EXPERTISE.
Leveraging our experience, we
implement the MITRE ATT&CK framework, which
provides a comprehensive knowledge base of adversary
tactics and techniques based on real-world
observations, aiding in threat modeling and defense.
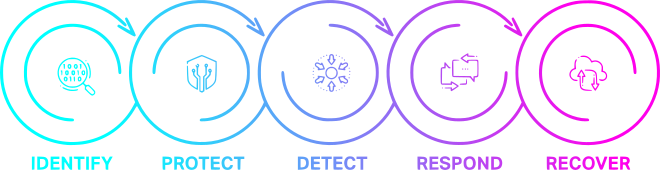
We utilize NIST CSF's structured guidelines to
manage cybersecurity risks by identifying,
protecting, detecting, responding to, and recovering
from cyber threats. Additionally, we apply the CIS
Controls, a prioritized collection of best practices
designed to secure IT systems and data.

We help you to prevent data loss and financial damage.
Our solutions against threats & risks.
>_ We apply a tailored set of tools, technologies, practices, expertise, and policies to meet your needs, regulatory compliance, and keep your business safe. We prevent threats, identify breaches, implement strategic actions, and deliver cost savings for your IT, Cloud or Security Team.
Risk and Compliance
- Risk Assessment and Management
- Security Audits and Compliance
- Privacy and Data Protection Consulting
- Supply Chain Security
Threat Discovery and Assessment
- Penetration Testing
- Threat Hunting
- Threat Intelligence
Network & InfraSec
- IDS & IPS Deployment
- Network Traffic Inspection
- Security Architecture Design
- Cloud Security
Endpoint & Apps Security
- Endpoint & Apps Security
- Application Security (DevSecOps)
- Data Protection and Encryption
Governance, Risk, and Compliance
-
Identity and Access Management (IAM)
-
Business Continuity and Disaster Recovery (BC/DR)
-
Physical Security
Security Awareness and Culture
- Training and Awareness
- Building Trust
Managed Security Services
- Ongoing management and monitoring of security technologies, through managed security service providers (MSSPs)
Detection and Response
-
Advanced Threat Protection
-
Incident response plans
-
Forensic analysis to understand the scope and impact of breaches
-
Assisting in recovery efforts and restoring normal operations
-
SIEM with SOAR integration
-
Vulnerability Management
Don't know where to start?
>_ We build a robust foundation to
secure your assets and data.
>_ IDENTIFY YOUR CRITICAL ASSETS
CLASSIFY YOUR KEY FINDINGS.
- Hardware: Servers, workstations, network devices, and other physical equipment.
- Software: Applications, operating systems, and databases that support your business functions.
- Data: Sensitive or valuable information, including customer data, intellectual property, and proprietary business data.
- Cloud Accounts: Cloud service providers, virtual machines, containers, storage solutions, and any cloud-based applications or infrastructure.
- Applications: Both on-premises and cloud-based applications that are integral to your business processes.
- Services: Third-party services, APIs, and integrations that interact with your systems and data.
- People: Key personnel whose roles are crucial for maintaining business continuity and security.
- Processes: Critical
workflows and operational procedures that
support core business activities.
Understanding
and prioritizing these assets helps you focus
your security efforts where they are needed
most and ensures that you can effectively
protect and manage them against potential
threats.
>_ REVIEW POLICIES AND PROCESS LOGS
GET READY FOR RISKS ASSESSMENTS.
Logs Collection and Processing:
- Sources: Gather logs from critical sources such as servers, network devices, firewalls, intrusion detection systems, applications, and cloud accounts.
- Types: Capture and process various types of logs, including cloudtrail logs, activity log, cloud audit logs, access logs, security logs, system logs, application logs, network devices logs and/or vpc logs.
- Storage: Ensure logs are stored securely, indexed for easy retrieval, and protected from tampering.
- Centralization: Implement centralized logging systems to streamline log management and analysis.
- Integration with SIEM: Integrate logs with a Security Information and Event Management system to enable real-time monitoring, threat detection, and incident response.
Detect and document findings, anomalies, misuse, and security gaps or weaknesses. We evaluate risks by identifying vulnerabilities and assessing the potential impact and likelihood of threats to your infrastructure, critical assets, and data.
All rights
Reserved © | ASTRÆA 2024 - DIGITAL ADVANCED SOLUTIONS
- D.A.S. SLU.
Made with from Andorra.
